How to Configure LFD Alerts in WHM for Enhanced Server Security
Introduction
Login Failure Daemon (LFD) is a critical security component in the Web Host Manager (WHM) control panel that helps system administrators monitor and protect their servers from potential security threats. LFD works in conjunction with ConfigServer Security & Firewall (CSF) to provide a comprehensive security solution for Linux servers. One of the key features of LFD is its ability to send alerts to system administrators when suspicious activity or security breaches are detected.
In this article, we will dive deep into LFD alerts in WHM, exploring the different types of alerts available, their importance, and how to configure them effectively to enhance your server’s security.
What are LFD Alerts?
LFD alerts are notifications sent by the Login Failure Daemon to system administrators when specific security-related events occur on the server. These alerts can range from informing about failed login attempts to warning about suspicious processes or system file changes. By promptly notifying administrators about potential security issues, LFD alerts enable quick response and mitigation of threats.
Importance of Monitoring LFD Alerts
Monitoring LFD alerts is crucial for maintaining a secure server environment. By keeping a close eye on these alerts, system administrators can:
- Detect and prevent brute-force attacks
- Identify compromised user accounts
- Spot suspicious processes or system file modifications
- Take timely action to mitigate security risks
- Ensure the overall integrity and stability of the server
Types of LFD Alerts in WHM
WHM offers several types of LFD alerts that cover various aspects of server security. Let’s explore each type in detail:
1. Excessive Resource Usage Alerts
LFD monitors running processes to check if they are consuming too many server resources. If a process exceeds the defined resource limits, LFD sends an alert to the administrator.
To enable or disable Excessive Resource Usage Alerts:
- Log in to WHM
- Navigate to “ConfigServer Security & Firewall” under the “Plugins” section
- Click on “Firewall Configuration”
- Locate the “PT_USERMEM” and “PT_USERTIME” parameters
- Set the desired values for memory and CPU time limits (in seconds)
- To enable alerts, set a non-zero value (e.g., PT_USERMEM = 200, PT_USERTIME = 1800)
- To disable alerts, set the value to 0 (e.g., PT_USERMEM = 0, PT_USERTIME = 0)
- Save the changes and restart CSF and LFD services
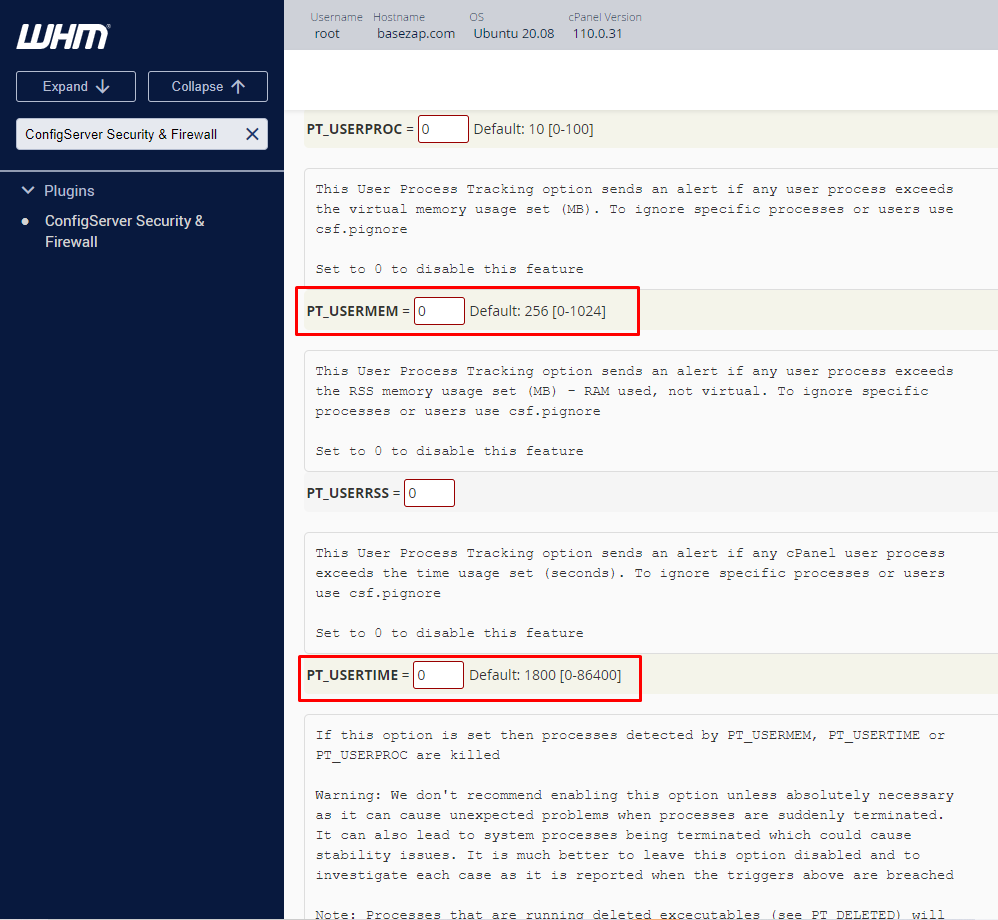
Default values:
- PT_USERMEM = 200 (200% of total memory)
- PT_USERTIME = 1800 (1800 seconds or 30 minutes)
2. System Integrity Alerts
LFD has a feature that monitors changes in certain system files to detect compromised files. If a file fails the integrity check, an alert is sent to the administrator.
System Integrity Alerts are enabled by default and do not require additional configuration. To disable them, you need to modify the LF_INTEGRITY value:
- Log in to WHM
- Navigate to “ConfigServer Security & Firewall” under the “Plugins” section
- Click on “Firewall Configuration”
- Locate the “LF_INTEGRITY” parameter
- Set the value to “0” to disable alerts or “1” to enable them
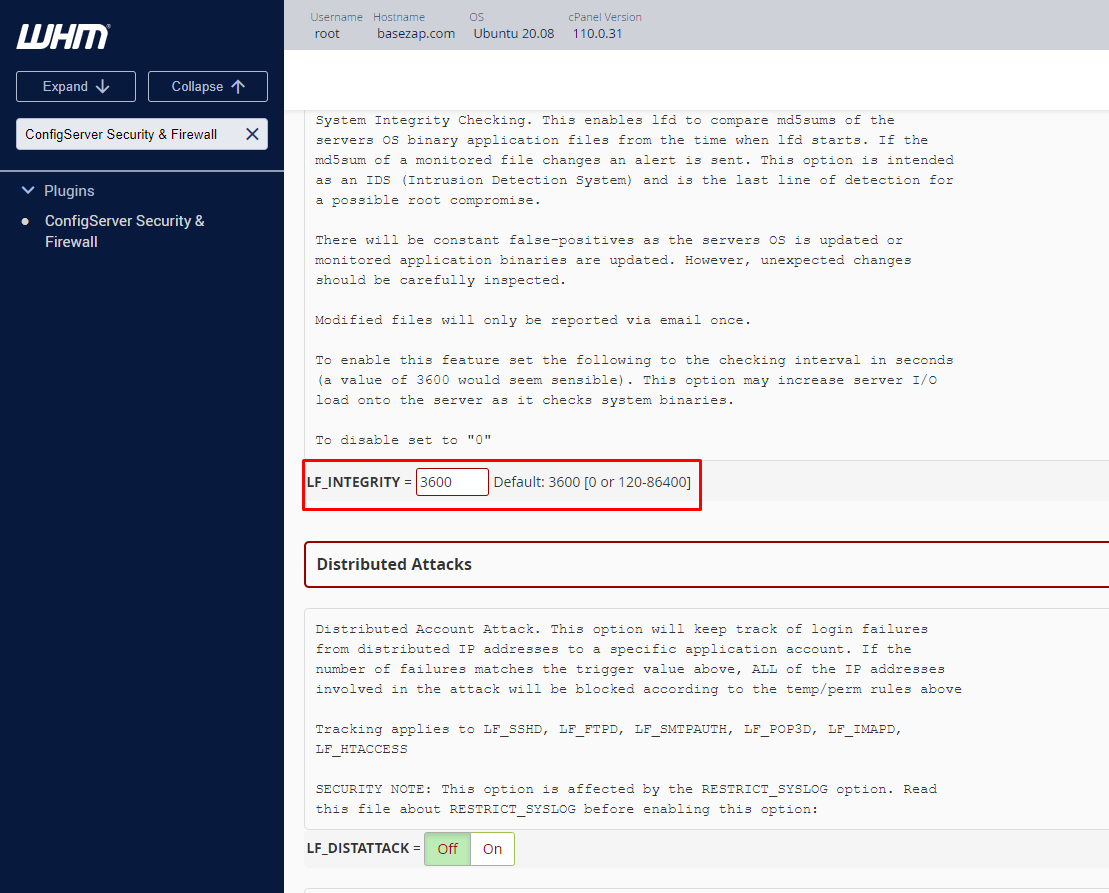
Default value: LF_INTEGRITY = 3600
Alternatively, you can also do this from SSH by modifying the CSF config file. To do so:
- Log in to your server via SSH
- Open the CSF configuration file (/etc/csf/csf.conf) with a text editor
- Locate the “LF_INTEGRITY” parameter
- Set the value to “0” to disable alerts or “1” to enable them
- Save the changes and restart CSF and LFD services
3. Suspicious Process Alerts
LFD can detect suspicious processes running on the server and send alerts to the administrator. These processes may have characteristics of exploits or malware.
To enable or disable Suspicious Process Alerts:
- Log in to WHM
- Navigate to “ConfigServer Security & Firewall” under the “Plugins” section
- Click on “Firewall Configuration”
- Locate the “PT_LIMIT” parameter
- Set the value to “1” to enable alerts or “0” to disable them
- Save the changes and restart CSF and LFD services
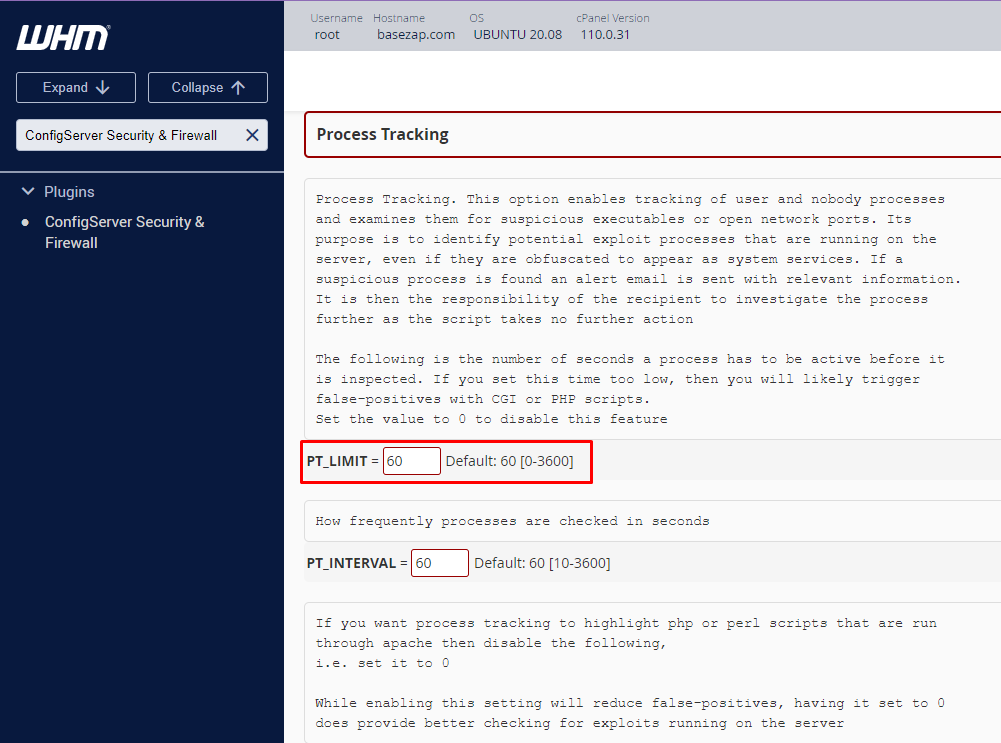
Default value: PT_LIMIT = 60
4. Login Alerts
LFD sends notifications when a user successfully logs in to the server via SSH, WHM, or cPanel. It also alerts when someone uses the “su” command or accesses the server using port knocking.
Login Alerts are enabled by default and do not require additional configuration. However, you can customize the alert recipients and notification templates in the “ConfigServer Security & Firewall” section of WHM.
5. Brute Force Login Alerts
LFD detects and blocks IP addresses that make repeated failed login attempts, which could indicate a brute-force attack. When an IP is blocked, an alert is sent to the administrator.
Brute Force Login Alerts are enabled by default and do not require additional configuration. However, you can adjust the number of failed attempts and the blocking duration in the “ConfigServer Security & Firewall” section of WHM.
6. Email Queue Size Alerts
LFD monitors the size of the email queue and sends an alert if it exceeds a specified threshold. A large email queue could indicate issues with email delivery or a potential spam outbreak.
To enable or disable Email Queue Size Alerts:
- Log in to WHM
- Navigate to “ConfigServer Security & Firewall” under the “Plugins” section
- Click on “Firewall Configuration”
- Locate the “LF_QUEUE_ALERT” parameter
- Set the desired threshold value for the email queue size
- To enable alerts, set a non-zero value (e.g., LF_QUEUE_ALERT = 100)
- To disable alerts, set the value to 0 (e.g., LF_QUEUE_ALERT = 0)
- Save the changes and restart CSF and LFD services
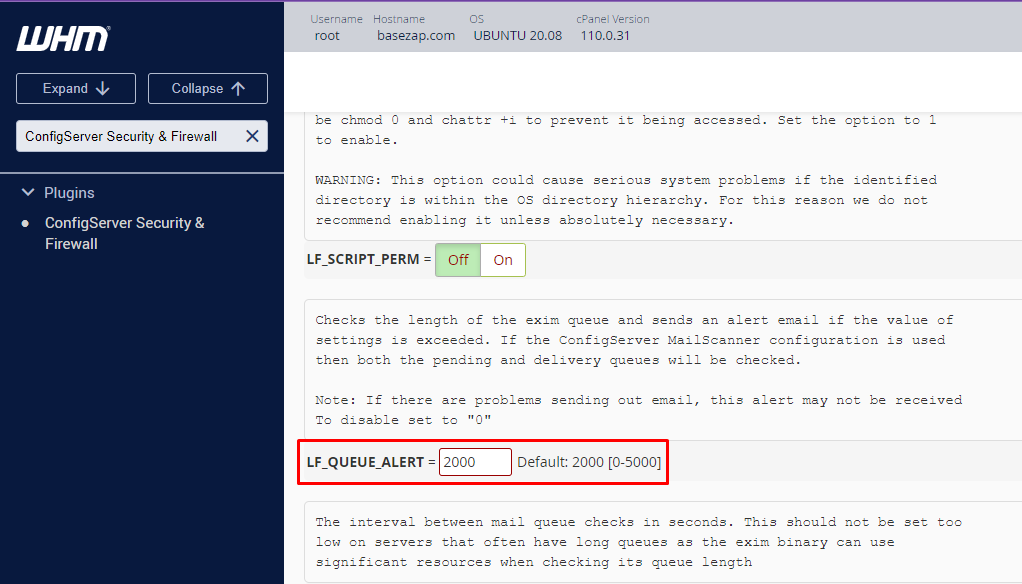
Default value: LF_QUEUE_ALERT = 2000
7. Email Script Alerts
LFD watches the mail log for emails containing scripts and sends an alert if such activity occurs repeatedly. This could indicate a compromised email account or a script-based attack.
Email Script Alerts are enabled by default and do not require additional configuration. However, you can customize the alert recipients and notification templates in the “ConfigServer Security & Firewall” section of WHM.
8. IP Block Alerts
LFD sends email notifications whenever it blocks an IP address. These alerts help administrators stay informed about potential security threats and take appropriate action. The following are the key parameters related to IP block alerts:
- LF_EMAIL_ALERT: Sends an email alert if an IP address is blocked by one of the triggers. Set to “1” to enable or “0” to disable.
- LF_PERMBLOCK_ALERT: Sends an email alert if an IP address is permanently blocked. This happens if the IP address has been temporarily blocked more than a few times (configured using LF_PERMBLOCK_COUNT). Set to “1” to enable or “0” to disable.
- LT_EMAIL_ALERT: Sends an email alert if the account exceeds a certain number of hourly logins per IP address. Set to “1” to enable or “0” to disable.
- LF_DISTFTP_ALERT: Sends an email alert if LF_DISTFTP is triggered. The LF_DISTFTP option tracks all successful FTP logins and blocks IPs suspected of being involved in an FTP distributed attack. Set to “1” to enable or “0” to disable.
- LF_DISTSMTP_ALERT: Sends an email alert if LF_DISTSMTP is triggered. Similar to LF_DISTFTP, but for SMTP. Set to “1” to enable or “0” to disable.
- CT_EMAIL_ALERT: Sends an email alert if an IP address is blocked due to connectivity tracking. Set to “1” to enable or “0” to disable.
- LF_NETBLOCK_ALERT: Sends an email alert if an IP network class is blocked. The conditions for such blocks can be configured in the CSF configuration file. Set to “1” to enable or “0” to disable.
Recommended Alert Thresholds
While the default values for LFD alerts are generally suitable for most servers, you may need to adjust them based on your specific requirements and server resources. Here are some recommended thresholds:
- PT_USERMEM: Set a value that aligns with your server’s memory capacity and the expected memory usage of your applications. A value between 200 and 500 is usually appropriate.
- PT_USERTIME: Set a value that allows enough time for your applications to execute while still detecting potential issues. A value between 1800 and 3600 seconds (30 to 60 minutes) is often suitable.
- LF_QUEUE_ALERT: Set a value that reflects the normal email volume of your server. A value between 100 and 500 is usually appropriate, depending on your server’s email traffic.
Remember to monitor your server’s performance and adjust these thresholds as needed to strike a balance between security and false positives.
Best Practices for Managing LFD Alerts
To effectively manage LFD alerts and maintain a secure server environment, consider the following best practices:
- Regularly review and investigate LFD alerts
- Set appropriate thresholds for resource usage and email queue size alerts
- Promptly address any suspicious activity or compromised accounts
- Keep CSF and LFD updated to the latest versions
- Customize alert recipients and notification templates as needed
- Use LFD alerts in conjunction with other security measures, such as strong passwords and regular system updates
Conclusion
LFD alerts are a vital component of server security in WHM, helping system administrators stay informed about potential threats and take timely action to mitigate risks. By understanding the different types of LFD alerts and configuring them effectively, you can enhance your server’s security posture and ensure a stable and protected environment for your websites and applications.
By understanding how to enable, disable, and configure LFD alerts in WHM, you can effectively manage your server’s security and stay informed about potential threats or issues.




